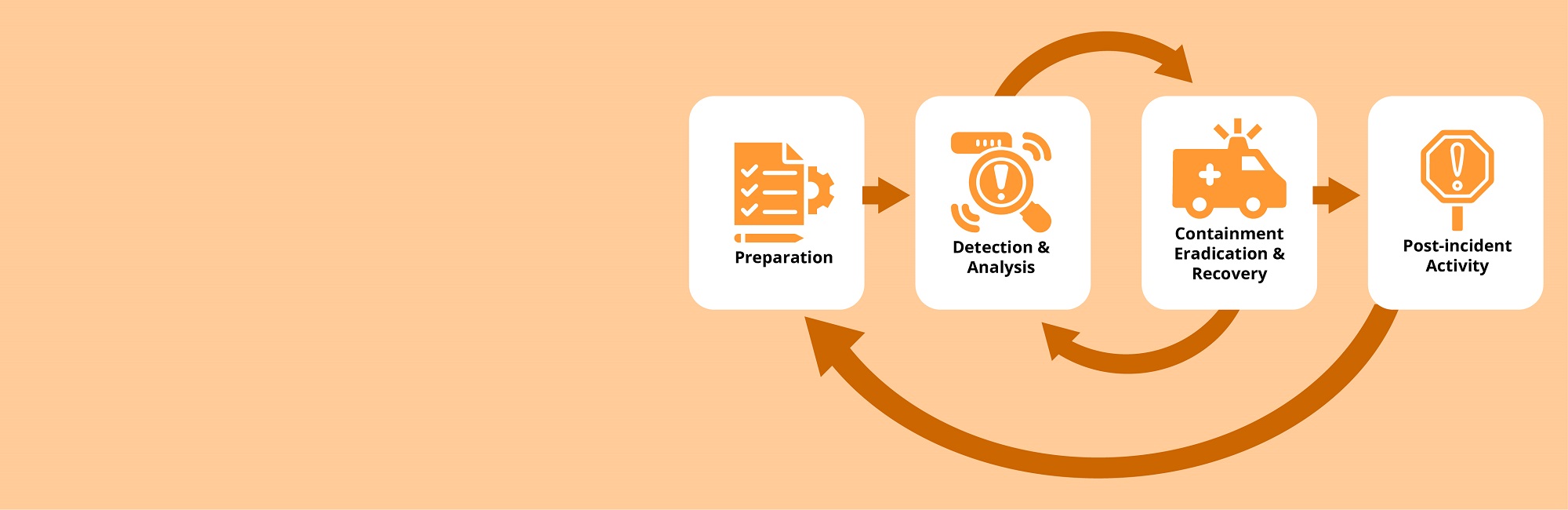
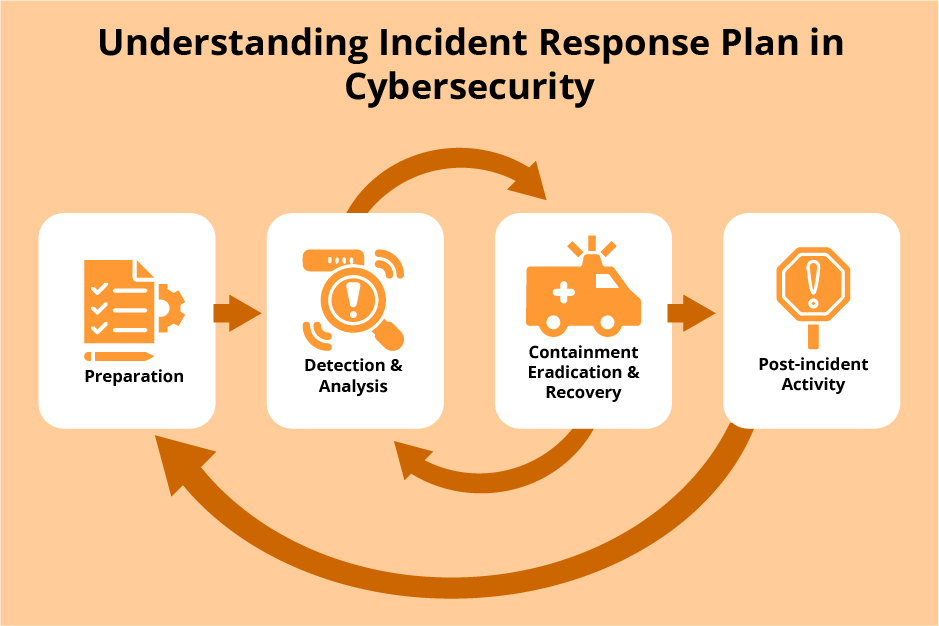
An incident response process is another important component of a clear strategy for dealing with security breaches. An incident response plan is a document that outlines the procedures and actions that an organization will take in the event of a security incident. It serves as a roadmap for detecting and responding to security incidents, minimizing their impact and reducing recovery time.
An incident response plan, similar to SIMP, guides how to handle security incidents with clear roles, reporting procedures, containment steps, and communication protocols for stakeholders.
Having both an incident response plan and Security Incident Management Plan helps organizations manage incidents and minimize impact while providing a framework for ongoing improvement to remain resilient against evolving threats.
An incident response process, also known as a Security Incident Management Plan (SIMP), is a predefined procedure that outlines the steps an organization should take in the event of a security breach. The SIMP plays a critical role in minimizing the impact of a security breach, locating and repairing the damage caused, and quickly restoring normal business capability.
In essence, the SIMP provides a roadmap for detecting, containing, and resolving security incidents. It establishes clear roles and responsibilities for the incident response team members, sets out procedures for reporting incidents, and defines the steps for containing and eradicating threats. The SIMP also includes a plan for communicating with stakeholders, such as customers and partners, to ensure transparency and build trust.
By having a SIMP in place, organizations can respond quickly and effectively to security incidents, minimizing the potential damage and disruption caused by such events. The SIMP also provides a framework for ongoing monitoring and improvement of security measures, ensuring that the organization remains vigilant and prepared in the face of evolving threats.
FR Secure claims that only 45% of organizations in their survey acknowledge that they have an incident response plan in place.
Cost: According to IBM, it takes, on average, 197 days to identify a breach and about 69 days to contain one effectively. The gap between detection and containment can cause up to $4 million, as per the same report. Small and medium businesses working with lean teams and tight budgets will surely perish with such large bills. Even large businesses will find it difficult to deal with such losses.
Preparation for the Unexpected: A security breach often happens at the most vulnerable times. Without proper planning, organizations may struggle to respond effectively and lose critical assets. However, data shows that most security attacks are executed just before long holidays like Christmas when the least or no staff is available to counter these attacks.
Along with a proper incident response process, there is a need for a team that can manage your security 24×7. Metaorange Digital helps you maintain your security and provide close 24×7 managed IT support in a complete package.
Minimizes Impact: Minimizing damage is critical in containing the damage. You should back up essential and sensitive data at multiple locations. Critical functions, processes, and workflows should be properly planned so that there is less reliance on single elements.
Compliance: The National Institute of Standards and Technology and many other regulatory organizations demand compliance with cybersecurity breaches, including incident reporting and response plans. IRP documents are critical components of such compliance.
The preparation phase involves creating an incident response team, defining roles and responsibilities, and preparing communication and reporting templates. A basic document created at this stage can be further modified to suit the customized needs of the organization. Several security guidelines exist from NIST, ISO, CIS, and many other organizations.
Confirming a breach is also very essential. Launching a full response during false flags can cost in terms of money, effort, and system resources. Proper monitoring systems, networks, and applications for signs of a breach are deployed and help determine the incident’s significance.
Networks, systems, endpoint devices, and other IoT(if present) must be isolated so that the hacker does not gain entire system access. It is unconventional, but in the case of an on-premise system, physical separation or air-gapping can also be used to disconnect systems physically in case the attacker is potent.
Reporting the incident to law authorities and others like insurance providers, regulators, and stakeholders is equally necessary. This helps you deny any liability in case of further damage. Reporting is also mandatory many times and is specified in insurance and regulatory documents. Further, reporting has to be done by a senior authority like the CIO or even the CEO. Identifying and delegating responsibility is also a critical component in creating an incident response plan.
Gathering information and analyzing it to identify all the weak points in the security perimeter is crucial in preventing further attacks. For example, endpoint security software always relies on a database of known malware, virus, and spyware which helps them focus more on newly evolving threats. Further, old data can also predict security incident patterns when analyzed with machine learning.
This is the most complex and the most unpredictable step of the entire incident response plan. Every threat is different from the other. Similarly, every organization has different types of approaches to dealing with cybersecurity threats. Before creating any response plan, it becomes necessary to leave some space for unconventional scenarios.
The recovery phase involves restoring normal business operations and conducting a post-incident review to identify areas for improvement.
The post-incident review phase involves evaluating the incident response plan, documenting lessons learned, and updating the plan to improve future incident response efforts.
Cloudflare 2022 DDoS Attack: Cloud-based cyber attacks are becoming common. Cloudflare published an incident report where a “crypto launchpad” was targeted with a record 15 million requests per second. The network used at least 6000 unique bots from several countries, including Russia, Indonesia, India, Colombia, and the USA.
Cloudflare contained the breach gradually. To counter the attack, a prior response protocol helped counter the attack. The response was coded as an algorithm in the response plan, making the request response time longer every time there were more data requests from the botnets.
Equifax Data Breach: In 2017, Equifax suffered a data breach that affected 147 million customers. The breach resulted from a vulnerability in Equifax’s web application software that allowed hackers to access sensitive customer information. Equifax’s incident response plan helped them to contain the breach and prevent further damage quickly, but the company still faced significant financial and reputational damage.
An incident response plan is a predefined procedure that outlines the steps an organization should take in the event of a security breach. It minimizes the impact of a breach, locates and repairs damage, and quickly restores normal business operations.
The plan includes preparation, identification, containment, reporting, analysis, eradication, recovery, and post-incident review phases. Having an incident response plan is important as it saves costs and helps prepare for unexpected breaches, minimizes impact, meets compliance requirements, and has been proven effective in real-life cases like Cloudflare’s 2022 DDoS attack and Equifax’s data breach in 2017.
Learn More: Cloud Transformation Services Of Metaorange Digital

Amit has over 16+ years of experience in IT and 5+ years in the field of DevOps, Cloud and automation technologies. He is a young entrepreneur with strong technical knowledge in Microsoft, Cloud, DevOps & Microservices and has expertise in highly scalable, available and fault-tolerant cloud architectures. He also has deep expertise in DevOps tools, Security, Cloud Migrations and deployment. Amit is a recognized Industry leader when it comes to migration of workloads from On-premise to Cloud, Configuration Management and Assessment.
15 February, 2023
Cloud Engineering