
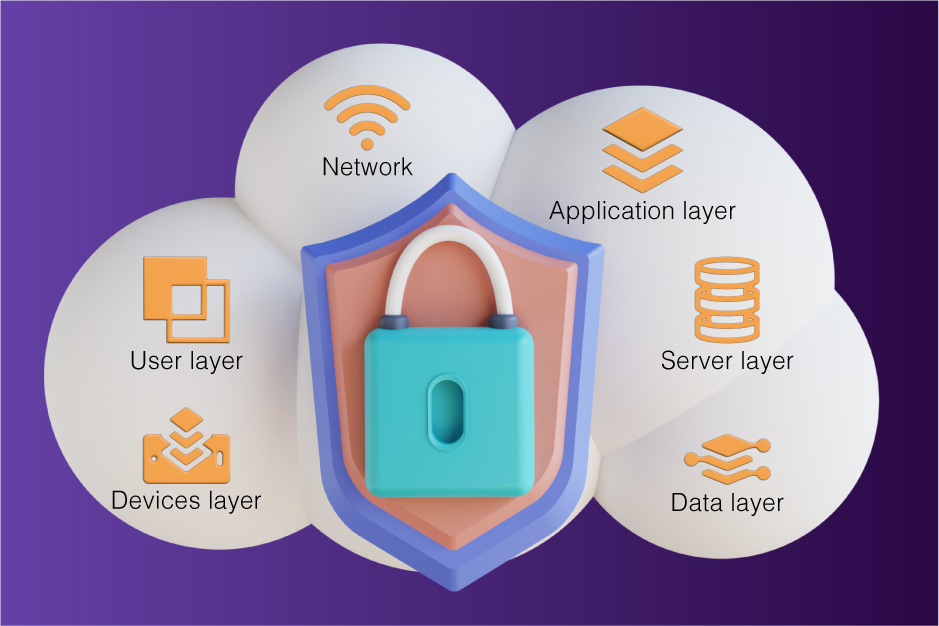
Layers of Cloud Security has been one of the most critical aspects of running businesses on the cloud. Over 88% of cloud-related security incidents were caused by human error. Further, there are growing challenges like DDoS attacks in the cloud. Multi-Layer Cloud Security (or 6 Layers of Cloud Security) helps you identify and effectively avoid these threats. Moreover, it is not that difficult to maintain cloud security measures.
Security is never an achievement but is always a process in continuity. Even large companies like Twitter, Samsung, and Meta have reported cybersecurity attacks in 2022. These businesses run the bulk of their operations on the cloud. An IBM report on the cost of Data Security shows that the average cost of a cybersecurity attack is almost $10 Million. Notably, one of the most well-known data breaches was on T-Mobile, causing damages of around $350 Million. Here is a list of Data Breaches so far in 2022 if you wish to explore them in detail.
Such attacks often prove to be fatal for small and medium-sized companies that do not have sufficient reserve funds to recover operational capabilities.
Layered security refers to security suits based on multiple components that are often independent of each other.
The layered approach to security is based on the Swiss Cheese Model. Here, each security layer is represented by a thin slice of cheese, and each hole on a layer of cheese represents the shortcomings of each layer. An attacker must exploit all the slices’ security flaws to get through the security. Since each flaw(hole) is covered by other layers of security, there is no single way of entry for the attacker.
An example is the commonly used 2-Factor Authentication.
Therefore, a multi-layered approach is highly effective due to cascading security layers. Further, optimizing those security layers on the basis of past experience helps you divert resources toward those threats which possess greater risk.
The network on which your cloud service operates should have common minimum security such as SSL, VPN security, intrusion detection, prevention of intrusion, and threat management response. Some of these features are often out of date because of user negligence. Further, there should be user-specific enhancements.
The application layer protects your web apps from DDoS attacks, HTTP floods, SQL injections, parameter tampering, etc.
The most common way of eliminating these threats is the usage of Web Application Firewalls(WAF), secure Web Gateway Services, etc. These safety features can come in the form of software or as a service.
The server layer is vulnerable due to many factors. Some of these are intrinsic, while some are extrinsic. Intrinsic factors such as bugs in the server OS or lowly encrypted servers pose high risks. Extrinsic server risks, such as denial of service or left open network access ports, also pose considerable risk.
Experts best handle the server layer security. Metaorange helps you secure your servers if you host them. It can also advise on shielding from server layer vulnerabilities that can come from your service provider.
Back-ups are critical for any business that has considerable data on the cloud. Further encryption of sensitive data is essential for the prevention of data breaches. Data retention and destruction should also be properly handled.
Automating this security layer through automated backups in frequent periods such as daily or weekly is easy. The frequency of backups should depend upon the data change rate on the cloud.
Devices are often the most insecure nodes in cloud security. Malicious agents can use data packets. The type of devices that are at utmost risk is handheld devices: mobiles, tablets, etc., and medical devices which use low-end operating systems.
It is most difficult to control the security of this layer because many devices do not support advanced security solutions.
Constant monitoring is of prime importance, along with taking frequent backups. Metaorange takes care of such situations with dedicated experts. We are the ones who do the heavy lifting so that you can better focus on your business.
The user layer security often lags due to human error. As much as 88% of cybersecurity incidents were caused by humans.
The solution for maintaining user-layer security is bringing a few best practices that bring human error to almost zero. Continuous education and workshops are essential in inculcating the best habits.
Security is essential for cloud-based businesses as their existence can be wiped out by unauthorized access. Cascading security layers in a way that covers every layer’s holes as described in the Swiss Cheese Model, can reduce overall vulnerability to a bare minimum. Metaorange can also help you monitor each layers of cloud security and fix unseen vulnerable points as they appear. This way, focusing on your business side becomes much easier.