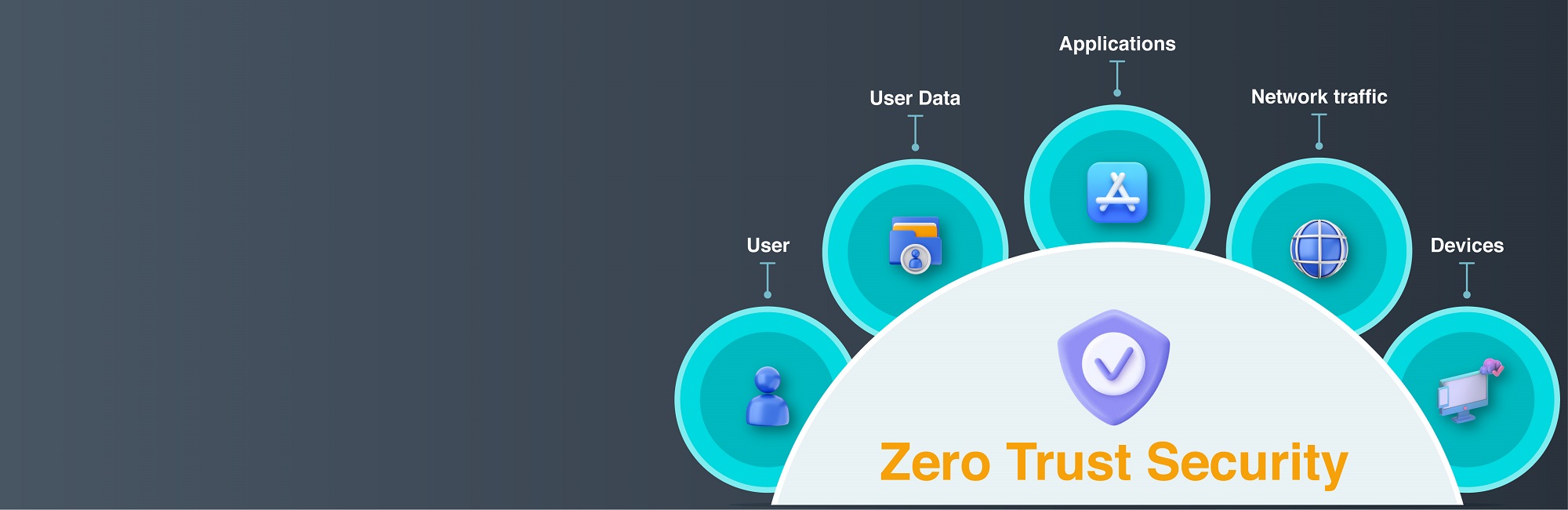
Protection against harm is of paramount importance in the online environment. Hackers, spammers, and other cybercriminals prowl the web, aiming to steal personal information and financial information, and damage companies. When protecting a company’s network, the zero trust security model is the way to go.
Statista states that 80% of users have adopted or are considering adopting the newest security model to prevent a data breach. Keep reading to learn more about the zero-trust security model, its guiding principles, and the ways in which it may help you stay one step ahead of cybercriminals.
What Is the Zero Trust Security Model?
A security infrastructure that requires all users, both within and outside the network, to be verified and approved before being given access to any resources, is referred to as the term “zero trust.”
The principle of “never trust and always verify” forms the basis of a zero-trust security model, which protects applications and data by ensuring that only authenticated and authorized people and devices can access them.
On the other hand, traditional methods of network security presume that an organization’s users are trustworthy while labeling any users from outside the company as untrustworthy.
The core notion of a zero-trust security architecture is to restrict an attacker’s privileges as they hop through one subnet to another, making it more challenging for them to travel laterally across a network.
The analysis of context (such as user identification and location, endpoint protection posture, and app/service being requested) establishes trust, which is then validated through policy checks at each step.
How Does Zero-Trust Work?
The Zero-Trust Security Model uses technologies such as identity protection, risk-based inter-authentication, dependable cloud workload innovation, and next-generation endpoint security. To verify a user’s true identity. In a zero-trust network, we consider all connections and endpoints as suspect. We determine access restrictions based on the context in which they were established.
Taking into account factors such as context, which might refer to the user’s function and location or the data to which they need access, can facilitate visibility and control over traffic and users in a particular environment.
For example, when an application or piece of software establishes a connection with a data set through an API, the zero-trust security framework checks and authorizes the connection. Both parties’ interactions should be consistent with the company’s established security protocols.
Zero Trust Security Principles
It is best to understand zero-trust security as a security model since it involves several concepts that demonstrate its usefulness. In this case, they are as follows:
Never Forget to Verify
The Zero-Trust Security Model is underpinned by the philosophy of “never trust, always verify,” which holds that no user or action can be trusted without providing further authentication.
Constant Checking and Making Sure
The idea of the zero-trust model is based on the adage “never trust, always verify.” This means that the process of verifying the identities and permissions of users and machines is ongoing and involves keeping track of who has access to what, how users behave on the system, and how the network and data are changing.
Zero trust has matured into a much more comprehensive approach. It is including a larger variety of data, risk concepts, and dynamic risk-based rules to give a solid framework for access choices and continual monitoring.
No Confidence in a Least-Privilege Trust Model
The foundation of the Zero-Trust Security Model is the concept of least privilege (POLP). This idea minimizes the attack surface by only granting users the permissions they need to perform a certain activity. Simply put, a member of the human resources department will not have access to the DevSecOps database.
Zero Trust Data
The purpose of zero trust is to guarantee the security of data throughout its transit between various endpoints. Such as computers, mobile devices, server software, databases, software as a service platform, etc. As a result, restrictions are imposed on how the data may be used after access is allowed.
Multi-Factor Authentication
Multi-factor authentication is another critical part of a zero-trust security architecture. Protecting your account using several verification steps, or “factors,” is called multi-factor authentication. Two-factor authentication typically consists of a password and a token generated by a mobile app.
Conclusion
Network security is nothing new, but the Zero Trust Security Model. It is relatively new, and it’s part of a larger philosophy that says you can’t just blindly trust your network. Instead, you should always assume that a link might be harmful and only gain faith in it once you have validated it. Consequently, you should consider reworking your security approach in light of the Zero Trust principle to lessen the likelihood of breaches and bolster your defenses.