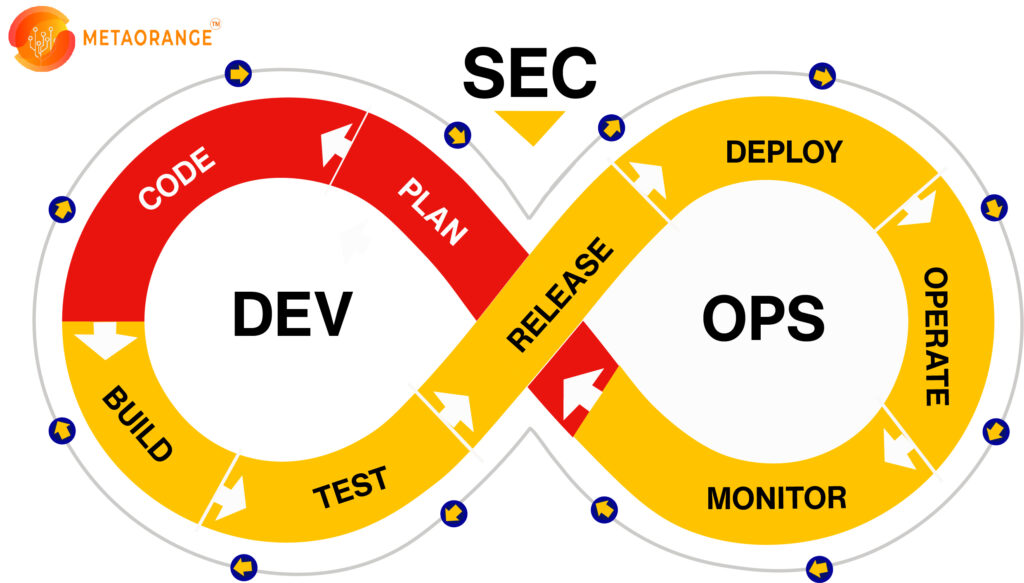
In most cases, security tests are done at the end of the application development life cycle, which is, of course, not the right way to leverage the DevSecOps Framework and develop a safe app. It is because detecting and fixing security concerns at the end of program development slows down the process. Also, detecting flaws at the end is a cumbersome task, resulting in the waste of both time and money.
The ideal approach to developing a safe app is to incorporate security from the very beginning of the software development life cycle. And that’s when DevSecOps comes in handy.
DevSecOps Framework is a tool used to fix security issues from the beginning of development.
If you want to learn more about DevSecOps Framework, read this post. In this post, we shall discuss the top 5 pillars of DevSecOps.
So, let’s get started…
What is DevSecOps Framework?
DevSecOps Framework is an integrated framework for managing projects in the realms of software development, network security, and IT operations. It aims to integrate security standards at all stages of the process. With DevSecOps Framework, different teams communicate with one another to produce more robust and secure software.
It is considered one of the best tools for finding and fixing security problems at an early stage. It makes finding flaws a breeze for developers. In addition, it also results in decreased development costs.
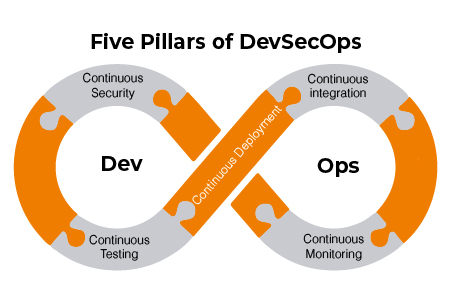
Let’s now take a look at the five pillars of DevSecOps Framework and see how they work together…
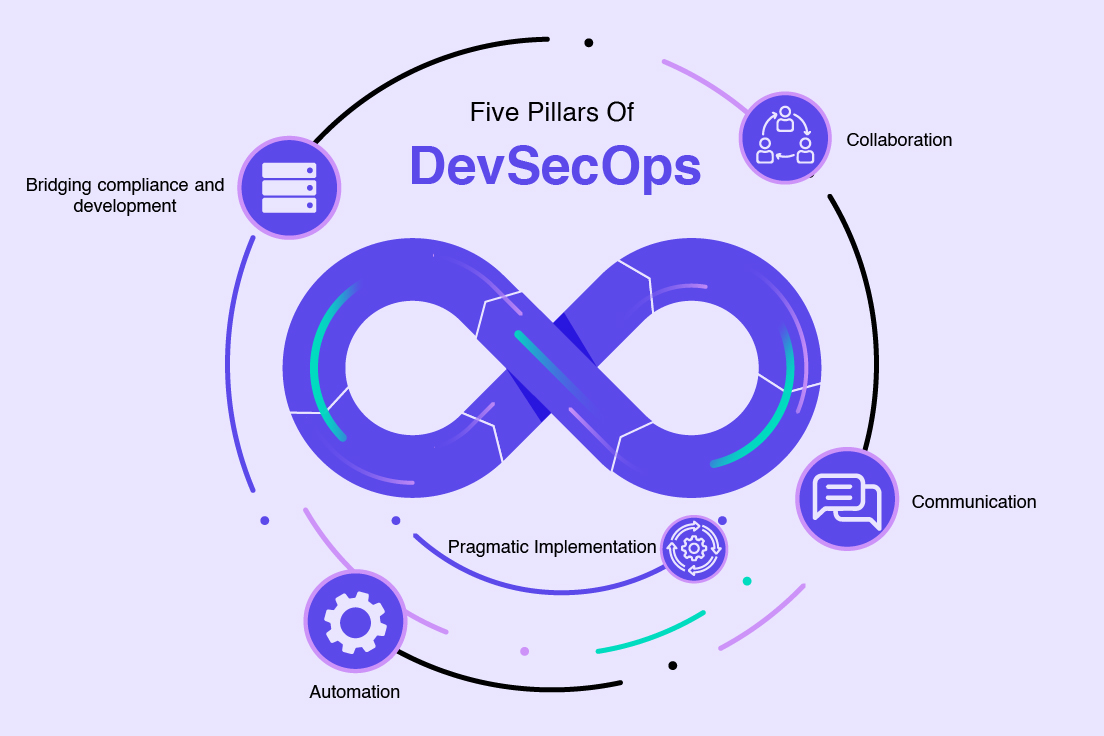
PILLAR NO. 1. Collaboration
Collaboration is the first and foremost pillar of DevSecOps Framework. DevSecOps Framework relies heavily on collaboration between development and operations teams. It transfers the responsibility for software and infrastructure security to the whole development and operations team.
The security team identifies and executes the minimum set of steps needed to generate high-quality, secure software fast while meeting all security standards.
It facilitates the automation of security chores and the gradual rollout of security capabilities. The developers are also expected to be aware of threats, as well as familiar with security standards and tools.
PILLAR NO. 2. Communication: DevSecOps Framework
Communication plays a crucial role when it comes to developing a flawless application. Without efficient communication, it is impossible to fulfil the requirements of the first pillar of the DevSecOps Framework methodology.
Therefore, it is vital for the development and operations teams to effectively convey information on security measures and procedures at each stage of software development.
App’s security team has to be in the loop with the development team at all times. Security experts should talk to the development team using terminology understandable to programmers. Only when developers are familiar with security flaws would they be able to write code in accordance with security procedures.
PILLAR NO. 3. Pragmatic Implementation
When it comes to developing a secure app, there is no “one size fits all” formula. Know that each software lifecycle has its unique structure, processes, and degree of maturity.
More often than not, organizations purchase tools and point solutions that are challenging to deploy and operationalize and ultimately do not deliver insights that can be used to minimize the underlying security risks.
To assure security, privacy, and trust in the digital world, companies need to take a pragmatic approach to security in DevSecOps Framework by adopting the framework-agnostic “Digital Security and Privacy Model” focused on Application Development.
This paradigm helps to fill a gap by improving communication between the many teams involved in application development in such a way that security becomes crucial at each stage.
PILLAR NO. 4. Bridging compliance and development
Transposing risk-related needs into easily measurable security requirements over time is challenging. Although security teams generate conditions to back up their risk-based approach, compliance needs are inadequately translated to DevSecOps Framework and product needs. Even with technical measures in place, it’s hard to prove security standards are met.
The key to bridging the compliance-development gap is finding applicable controls, interpreting them into software measurements, and determining inflection points in the application lifecycle where all these controls may be automated and assessed to improve risk mitigation and compliance.
PILLAR NO. 5. Automation
Last but not least, the development process should begin with security automation. It will aid in integrating security measures into the development process of applications, reducing the risk of security challenges during the creation of the applications.
Each stage of the continuous integration and continuous delivery processes within the DevSecOps Framework should include automated security testing and analysis. Doing so will ensure a safe app in the end.
Automated testing methodologies can be used to test applications and APIs in real time. Automation technologies added throughout the development process will give a red alert when there is a security threat. The teams will then first fix the error before proceeding further. This will save a significant amount of time and money in application development.
Summing up…
So these are the five pillars of DevSecOps Framework. These pillars must be taken into account when designing, implementing, and managing DevSecOps Framework.
DevSecOps Framework has undeniably changed the game when it comes to managing security for applications at every stage of development.
Since its debut, DevSecOps has been a desirable framework for a variety of reasons, including the enhancement of security, the acceleration of the development process, and the reduction of the cost of development.
Hopefully, this article has been enlightening for you and helped you better understand DevSecOps Framework and how to incorporate it into your software development life cycle.
Thanks for reading!
Learn More: DevOps Services of Metaorange Digital