What is Kubernetes Containers Orchestration?
Kubernetes is a top open-source tool for automating the deployment and management of containerized applications. It offers a robust and scalable infrastructure, streamlining it efficient container orchestration for optimal performance and scalability in modern, cloud-native development. This allows developers to focus on building applications without worrying about diverse underlying systems.
Containers provide a lightweight and portable solution, ensuring consistent environments and seamless execution across different setups. They simplify development and deployment, allowing developers to concentrate on application building. In software development, orchestration, exemplified by Kubernetes, efficiently automates tasks like load balancing and resource allocation, providing a user-friendly framework for managing applications across clusters of hosts
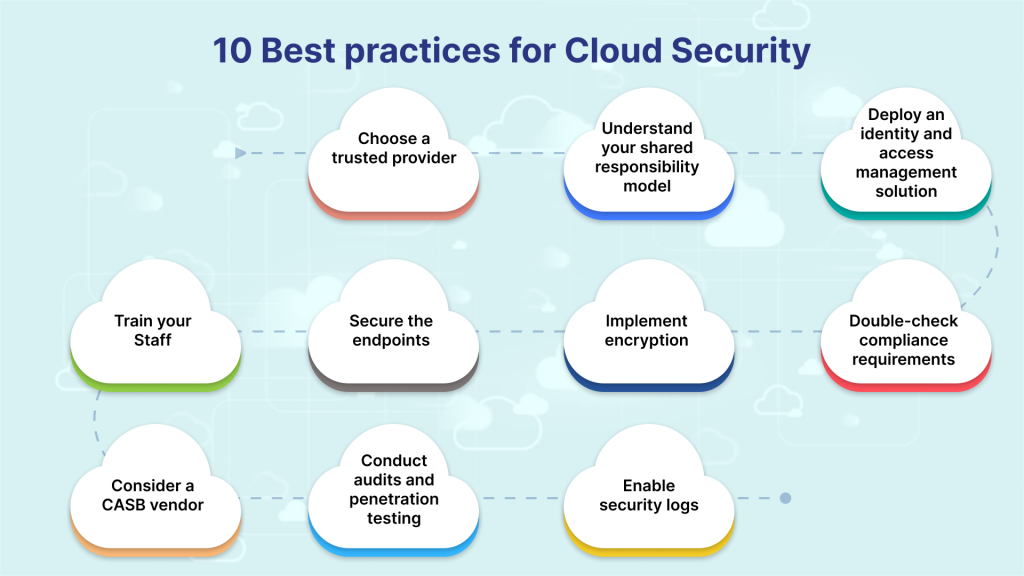
Best Practice for Effective Kubernetes Management
Kubernetes Container orchestration systems provide the tools and functionalities to automate the deployment, scaling, and management of containers. Kubernetes, often referred to as K8s, is an open-source container orchestration platform developed by Google. It allows you to manage and scale containerized applications utilizing the power of automation.
Effective Kubernetes management hinges on key practices, prioritize declarative configuration, set resource limits, and utilize native scaling and load balancing. Regular monitoring, proactive fault tolerance, and staying updated on security ensure a secure and resilient environment. Automation for repetitive tasks and a collaborative, well-documented culture enhances the efficiency of it deployments.
Container orchestration offers numerous benefits that help improve the efficiency and scalability of your applications.
What are the Key Advantages of Kubernetes Container Orchestration?
Kubernetes container orchestration offers key advantages such as automatic scaling, efficient resource utilization, and seamless deployment, making it a pivotal tool for managing and scaling containerized applications. Its ability to automate complex tasks simplifies container management, enhances reliability, and facilitates the efficient operation of containerized environments.
1. Simplified Deployment and Scaling
Kubernetes simplifies container orchestration by enabling easy deployment and scaling. Through declarative configuration, defined in manifests, users articulate the desired state of their application, specifying parameters like replica count and resource requirements. It automates the alignment of actual and desired states, continuously monitoring application health. It automatically restarts failed containers, ensuring uninterrupted operation. Furthermore, with built-in scaling features, it enables dynamic adjustment of application scale in response to demand, providing a seamless and efficient orchestration solution.
2. Improved Resource Utilization
Kubernetes and similar container orchestration platforms enhance resource utilization by intelligently distributing containers across nodes based on availability and requirements. They prevent overload by ensuring an even distribution and provide tools for setting resource limits (maximum usage) and requests (minimum requirements) for each container. This fine-tuning optimizes resource allocation, minimizing contention among containers and improving system performance.
3. Service Discovery and Load Balancing
Kubernetes simplifies modern application development with microservices, each in its container. It streamlines communication via built-in service discovery and load balancing, assigning unique IP addresses and hostnames. This simplification enhances scalability. Additionally, its integrated load balancer ensures high availability and efficient traffic distribution across service replicas, adapting seamlessly to changes in replica numbers.
4. Fault Tolerance and Self-Healing
Kubernetes offers inherent fault tolerance and self-healing features by actively monitoring application health and managing container failures. In the event of a container becoming unresponsive or crashing, it automatically initiates a restart. Additionally, if a node fails, it swiftly reschedules affected containers on other available nodes, ensuring continuous application operation despite potential failures. This robust fault tolerance and self-healing mechanism significantly enhance the reliability and availability of applications.
5. Application Portability and Vendor Lock-In Avoidance
Kubernetes, as a leading container orchestration tool, supports application portability across diverse environments without modification. Whether on-premises, in the cloud, or in hybrid setups, it ensures seamless container deployment, providing flexibility and preventing vendor lock-in. As an open-source platform with strong community support and endorsement from major industry players, it is a reliable and widely adopted solution. This versatility enables straightforward migration of applications between different cloud providers or hosting environments, giving users the freedom to choose the optimal infrastructure without being tied to a specific vendor.
Conclusion
Kubernetes Container orchestration, notably with tools like Kubernetes, offers key advantages for modern application development. It streamlines deployment, enhances resource utilization, and provides essential features like service discovery, load balancing, fault tolerance, self-healing, and application portability. As containerized applications grow in complexity, orchestration becomes essential for managing them at scale. It, with its extensive ecosystem and active community, stands as the preferred and solidified container orchestration platform of choice.
Read our blog page for such useful contents.